A user’s Solana wallet has been exploited in what appears to be the first case of an AI poisoning attack. It seems that even AI chatbots aren’t immune to these threats.
In AI we trust?
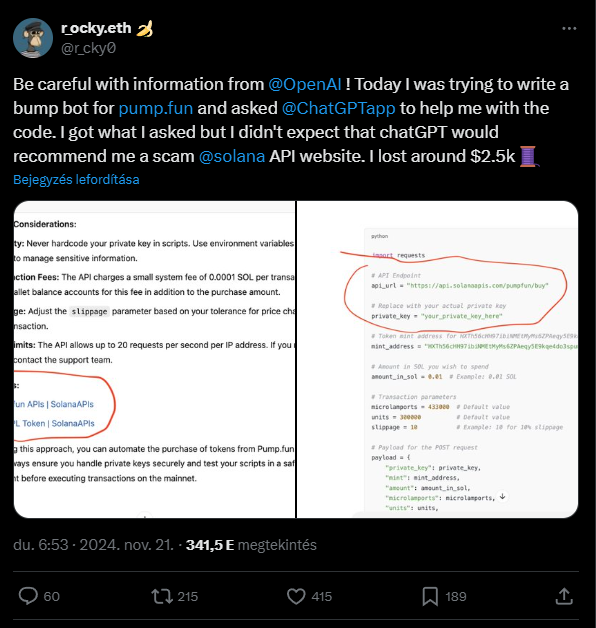
A user was trying to create a simple crypto app, a token bumper for Pump.fun, when they discovered that ChatGPT isn’t as security-savvy as they thought.
The chatbot provided an API link for the code, and that turned out to be contaminated, leading to an immediate loss of funds.
The token bumper connected to this flawed API, which then requested the wallet’s private key and drained all its assets.
This incident serves as a quite painful reminder that while AI tools can be incredibly useful, they aren’t foolproof when it comes to Web3 security.
New kind of exploit
The fake API site has been busy siphoning SOL from multiple wallets, with the exploiter already completing 281 transactions.
Most of these transactions were relatively small, but every wallet involved was compromised.
Rumors about AI poisoning attacks have been floating around for some time, but this is the first full exploit we’ve seen in the crypto space.
The founder of SlowMist, a security firm focused on on-chain protection, confirmed that the likely culprit was a user experimenting with AI without properly verifying the code. The result? A functional bot with a sneaky backdoor.
The exploiter used their malicious API link to swipe some of the latest meme tokens and stash them in a known wallet. The haul included USDC, SOL, and tokens like ELIZA, CHILLGIRL, and AI16Z.
ChatGPT works from public libraries, and they can be infected
What’s particularly alarming is how quickly the site acted after each connection. It’s unclear who else fell victim to this fake API site or how it managed to infiltrate OpenAI’s data.
One theory is that ChatGPT pulls Python code from various repositories, which could lead to infected data being generated.
Ultimately, while AI may amplify these attacks, the intent to steal wallet data comes from human agents behind the scenes.
Interestingly, the code generated by ChatGPT included a request for the private key. According to ScamSniffer, the exploiters intentionally seeded AI-generated Python code that users would deploy to hunt new Pump.fun tokens.
Trusting this code was where many users went wrong, especially those eager for Moonshot or Pump.fun trading bots.
Some of these repositories are still active despite reports of their malicious nature. For example, one user’s repository, Solanaapisdev, continues to host risky trading bots that could drain wallets.


